Darktrace End of Year Threat Report reveals shifting threats
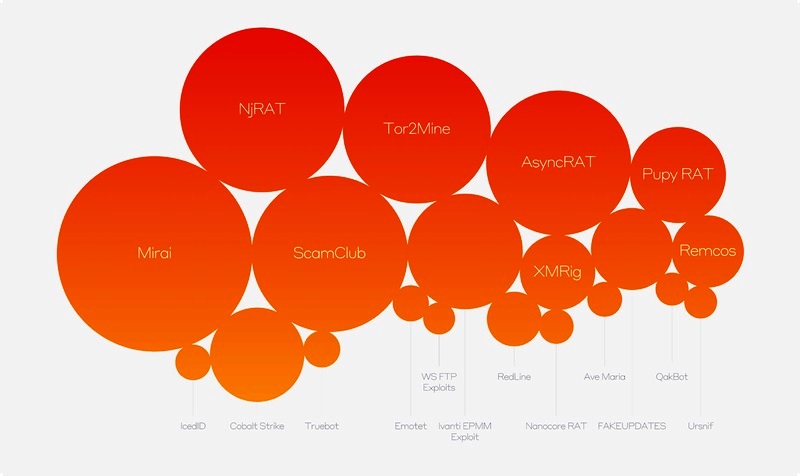
Above: The diagram represents Darktrace detections containing indicators of compromise (IoCs) that have been associated with particular MaaS and RaaS threats. The size of the bubble displayed relates to the frequency of detections observed across the Darktrace fleet.
Courtesy Darktrace
These insights, observed by Darktrace’s unique Self-Learning AI across its customer fleet, shed light on rapid shifts in the cyber security landscape and new techniques adopted by attackers attempting to sidestep traditional defences.
The findings show that as-a-Service attacks continue to dominate the threat landscape, with Malware-as-a-Service (MaaS) and Ransomware-as-a-Service (RaaS) tools making up the majority of malicious tools in use by attackers. As-a-Service tools can provide attackers with everything from pre-made malware to templates for phishing emails, payment processing systems and even helplines to enable criminals to mount attacks with limited technical knowledge.
The most common as-a-Service tools Darktrace saw in use from July to December 2023 were:
- Malware loaders (77% of investigated threats[1]), which can deliver and execute other forms of malware and enable attackers to repeatedly target affected networks.
- Cryptominers (52% of investigated threats), which use an infected device to mine for cryptocurrency.
- Botnets (39% of investigated threats), enrol users in wider networks of infected devices, which attackers then leverage in larger-scale attacks on other targets.
- Information-stealing malware (36% of investigated threats), malicious software like spyware or worms, designed to secretly access and collect sensitive data from a victim’s computer or network.
- Proxy botnets (15% of investigated threats), more sophisticated botnets that use proxies to hide the true source of their activity.
The report also reveals a changing of the guard. In its First 6: Half-Year Threat Report, Darktrace identified Hive ransomware as one of the major Ransomware-as-a-Service attacks at the beginning of 2023. With the dismantling of Hive by the US government in January 2023, Darktrace observed the rapid growth of a range of threats filling the void, including ScamClub, a malvertising actor notorious for spreading fake virus alerts to notable news sites, and AsyncRAT, responsible for attacking US infrastructure employees in recent months.
Attackers shift to advanced solutions to bypass conventional security measures
As businesses continue to rely on email and collaboration tools for communication, methods such as phishing continue to cause a headache for security teams. Darktrace detected 10.4 million phishing emails across its customer fleet between the 1st September and the 31st December 2023.
However, the report also highlights how cybercriminals are embracing more sophisticated tools and tactics designed to evade traditional security parameters. One example is the rise of Microsoft Teams phishing in which attackers contact employees through Teams, posing as a co-worker and tricking them into clicking malicious links. In one case in September 2023, Darktrace identified a suspected Teams phisher attempting to trick users into clicking a SharePoint link that would download the DarkGate malware and deploy further strains of malware across the network.
Another new trend identified is the growth of malware developed with multiple functions to inflict maximum damage. Often deployed by sophisticated groups like cyber cartels, these Swiss Army knife-style threats combine capabilities. For example, the recent Black Basta ransomware also spreads the Qbot banking trojan for credential theft. Such multi-tasking malware lets attackers cast a wide net to monetise infections.
"Throughout 2023, we observed significant development and evolution of malware and ransomware threats, as well as changing attacker tactics and techniques resulting from innovation in the tech industry at large, including the rise in generative AI. Against this backdrop, the breadth, scope, and complexity of threats facing organizations has grown significantly,” commented Hanah Darley, Director of Threat Research, Darktrace. “Security teams face an up-hill battle to stay ahead of attackers, and need a security stack that keeps them ahead of novel attacks, not chasing yesterday’s threats.”
Download the 2023 End of Year Threat Report at darktrace.com/threat-report-2023.