UK and allies warn of cyber attack vulnerabilities

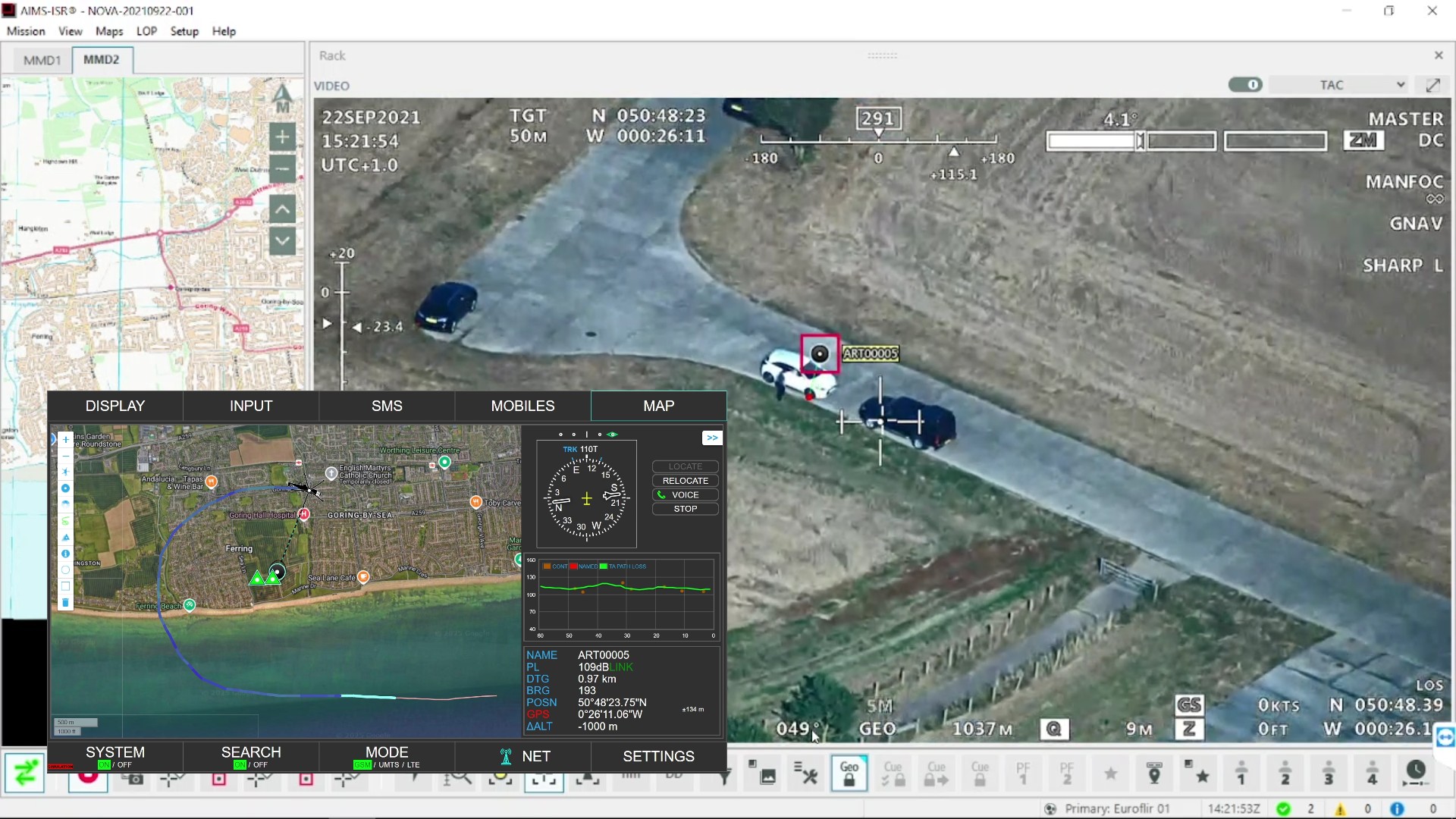
Above: The National Cyber Security Centre (NCSC), Nova South, London.
Image by Simona Flamigni / copyright Shutterstock
In a new advisory, the National Cyber Security Centre (NCSC) – a part of GCHQ – alongside partners in Australia, Canada, New Zealand and the United States, shared a list of the top 15 routinely exploited vulnerabilities of 2023.
Of these vulnerabilities, the majority were first exploited as zero-days – weaknesses that were recently discovered and where a fix or patch was not immediately available from the vendor – allowing attackers to conduct cyber operations against higher-priority targets.
This trend, which the NCSC has continued to observe into 2024, marks a shift from 2022 when less than half of the top list was initially exploited as zero-day vulnerabilities.
The advisory strongly encourages enterprise network defenders to maintain vigilance with their vulnerability management processes, including applying all security updates in a timely manner and ensuring they have identified all assets in their estates.
It also calls on technology vendors and developers to follow advice on implementing secure-by-design principles into their products to help reduce the risk of vulnerabilities being introduced at source and being exploited later.
Ollie Whitehouse, NCSC Chief Technology Officer, said: “More routine initial exploitation of zero-day vulnerabilities represents the new normal which should concern end-user organisations and vendors alike as malicious actors seek to infiltrate networks.
“To reduce the risk of compromise, it is vital all organisations stay on the front foot by applying patches promptly and insisting upon secure-by-design products in the technology marketplace.
“We urge network defenders to be vigilant with vulnerability management, have situational awareness in operations and call on product developers to make security a core component of product design and life-cycle to help stamp out this insidious game of whack-a-mole at source”.
All vulnerabilities listed have had patches and fixes made available from the vendors to help mitigate the risk of compromise.
In the case of zero-day vulnerabilities, where exploitation is rife it is vital organisations have a process in place to install vendor updates at pace after they become available to minimise the opportunity for attackers.
In addition to the top list, the advisory also details a further 32 vulnerabilities that were routinely exploited in 2023.
If mitigation steps have not already been taken, network defenders should follow vendor advice in each case and check for indicators of compromise before applying updates.
Advisory jointly published by:
- NCSC
- US Cybersecurity and Infrastructure Security Agency (CISA)
- US Federal Bureau of Investigation (FBI)
- US National Security Agency (NSA)
- Australian Signals Directorate’s Australian Cyber Security Centre (ACSC),
- Canadian Centre for Cyber Security (CCCS)
- New Zealand National Cyber Security Centre (NCSC-NZ)
- Computer Emergency Response Team New Zealand (CERT NZ)
View full advisory on CISA's website